A Brand’s ability to market its products creatively is vital to its success. Customers are exposed to thousands of communications every day an expertly constructed product...


Azerbaijan’s capital, Baku, was the location for the inaugural “Youth Cybersecurity Forum 2025,” held at the Baku Convention Center. According to a report by News.Az, citing...


1. Definition Here’s a simple analogy: 2. Scope 3. Applications 4. Complexity 5. Flexibility 6. Human Interaction 7. Examples 8. Key Differences at a Glance Aspect...


The type of insider threat that acts maliciously with motive and intent is known as a Malicious Insider or Intentional Insider Threat. These individuals deliberately exploit their authorized access...


Introduction In the era of artificial intelligence (AI), deepfake technology has evolved beyond video manipulation to include highly realistic voice cloning. Deepfake voice scams, also known...


In what seems to be an irreversible paradigm shift, AI and ML have rapidly transitioned from industry-specific jargon to instrumental technological breakthroughs that are redefining operating...


Phishing emails are fraudulent messages designed to trick recipients into revealing sensitive information like passwords, credit card numbers, or social security numbers. They often appear to...
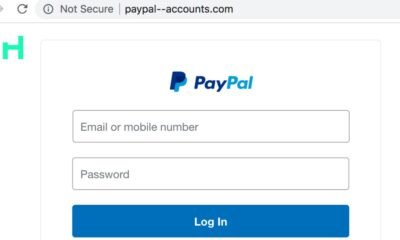

If you receive a suspicious email that claims to be from PayPal, follow these steps to report it: 1. Identify a Suspicious Email 2. Forward the...


Phishing is a cybercrime in which an attacker sends a fraudulent message designed to trick a user into opening it, clicking on a link, or downloading...


Yes, you are correct. When you receive a text message that there is a problem with your bank account and you are required to click on...